So, Who Are The Best VPNs of 2018?
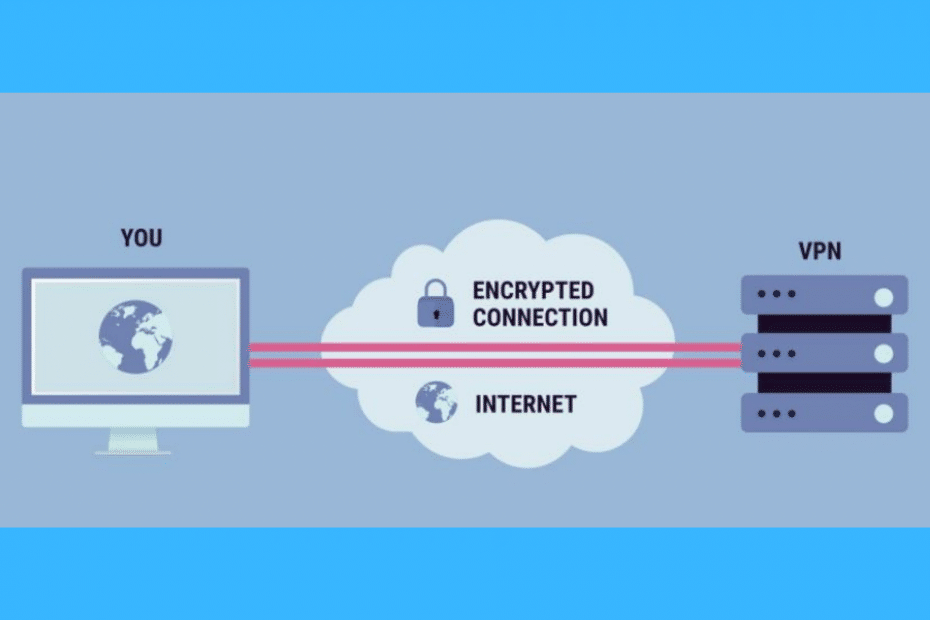
Due to the issue of online privacy, VPNs or Virtual Private Networks continue to gain popularity. In fact, there are hundreds of them in the market. However, not all of them gives you the online security and protection that you highly needed.
Some of them log your activities that they can use to potentially create harm or use it to their own advantage. These are the kinds of VPNs that you should stay away from.
To help you decide which is the best
Some of the considerations include:
- Documenting or keeping logs and what kinds of logs they keep
- Monitoring usage and ways on how they limit user usage
- File sharing sites that are allowed on their servers like BitTorrent
- Their payment method and the security of it
- Availability of kill switches, if there is connection leak
- In-house or outsource servers
- Offering virtual locations
Our List Of The Best VPNs of 2018
IP VANISH
When it comes to keeping logs, they don’t document activities or even use timestamps. They use an automated tool that limits device connection up to six devices. They have also optimized their servers only for file sharing, so users can stream without uninterrupted speed and with enough online protection.
They use PayPal which requires basic information. They also use Bitcoin, which makes the client more anonymous since no personal information is involved.
They also have an automatic kill switch in case of a DNS leak. When it comes to managing their servers, they use a hybrid model, which means they control most of their servers, but outsource with premium data centers for higher security.
They don’t offer virtual locations. They have 3000 servers in over 59 countries.
CyberGhost
Just like IP Vanish, it is in their policy to not keep logs of their users. They use a system to identify usage abuse. They also allow BitTorrent and other file-sharing sites. But, they direct it to a second
Payments available to them are Credit Card, Amazon, Google, Bitcoin, PayPal, among others. Since they don’t keep logs of their users, they also don’t keep payment data nor it is linked to any user activity.
They also have killed switch, DNS leak protection, and other tools and systems in case of a connection leak.
They use third-party data centers from business partners that they highly trust. They don’t also serve virtual locations. They have 3172 servers in over 43 locations.
StrongVPN
This
Connected devices are not limited, so you can connect as many devices as you can. However, as they have said, they can block any abusive traffic. They also don’t sensor traffic. Thus, BitTorrent and other file sharing are allowed.
They use PayPal and recommends Bitcoin if their users would like complete anonymity on their transactions.
StrongVPN also has a number of ways to protect their users from potential leaks. They have a Network Lock feature whenever a connection drops or VPNs have a leak. They have their own DNS on their servers, thus they are not using any third party DNS.
They cater to virtual locations in areas that are difficult to find servers. They have 2,000 servers in over 94 countries.
VyprVPN
Just like the other VPNs, VyprVPN does not keep any activity or traffic logs. They have a strict no logging policy.
To identify activity abuse, they use a customized script to monitor network performance. They also allow P2P traffic. Thus, BitTorrent and other file-sharing sites are allowed. They do not reroute or block these kinds of traffic. They also accept over 200 payment options. Some are PayPal, credit card, Bitcoin and other cryptocurrencies.
In protecting users from potential leaks, they have features that automatically disable IPv6 and block potential DNS leaks. They have a full connection kill switch to protect
They take full control with their servers and only partners with trusted data centers who meet their security requirements.
They do not use virtual locations. They have thousands of servers in 55 countries.
PrivateInternetAccess
They are not keeping any activity or session logs. Once the session has ended, all the data will be deleted. Real abuse is being monitored by humans. They use tools for limiting activity use.
They also allow other file-sharing sites like BitTorrent.
Some of their integrated payments are PayPal, Bitcoins, and Payza. Other payment methods can be requested. They also don’t store any payment information.
They also have kill-switch feature. In fact, they have different various types of kill switches from sleep, shutdown or wipe your hard disk.
They don’t use a third party. They have their own server, switch, and cable. They cater to Sweden and do not use virtual locations.
HideIPVPN
Logs for user activities, IP addresses, and DNS logs are not kept. They have a strict “no log” policy. They monitor usage by keeping a log of a single timestamp of the last login attempt. This is to ensure that the user is not making an excessive number of connections.
They allow P2P traffic, but it is limited to their paid products. Thus, P2P traffic is not allowed on their free versions.
Just like the others, their most common payment method is PayPal and Bitcoin. And all payment information is not logged or not linked to the user to provide anonymity. They also have kill switch feature that is both available in MacOS and Windows.
They have their own server, but they also have additional servers from trusted data centers that meet their quality and security requirements. They don’t use virtual locations or fake servers. They have 120 servers in over 14 countries.
SecureProXPN
They don’t keep a log of activities, timestamps, IP addresses, and other data sessions as well as DNS requests among others. Their no-log policy can be found in their terms of service.
They use a Blind Operator tool which means that they cannot monitor all the activities or traffic. However, abuses are being tracked using UDP filtering. They also allow P2P traffic like BitTorrent and other file-sharing sites. They are strong believers of net neutrality.
Some of their payment options include Bitcoin, Bitcoin Cash, Litecoin, and other cryptocurrencies. You can also use PayPal or credit cards. They don’t keep sensitive information and they only provide the reference code for order confirmation.
For maximum network quality, they own their own hardware, servers, and switches. They only operate in five locations namely UK, Sweden, Spain, Canada, and the USA. And they don’t have virtual locations.
These are just some of the VPNs that you can choose to use. There are other VPNs out there if these don’t meet your needs for any reason.